什麼是 iSCSI Initiator,它如何運作?
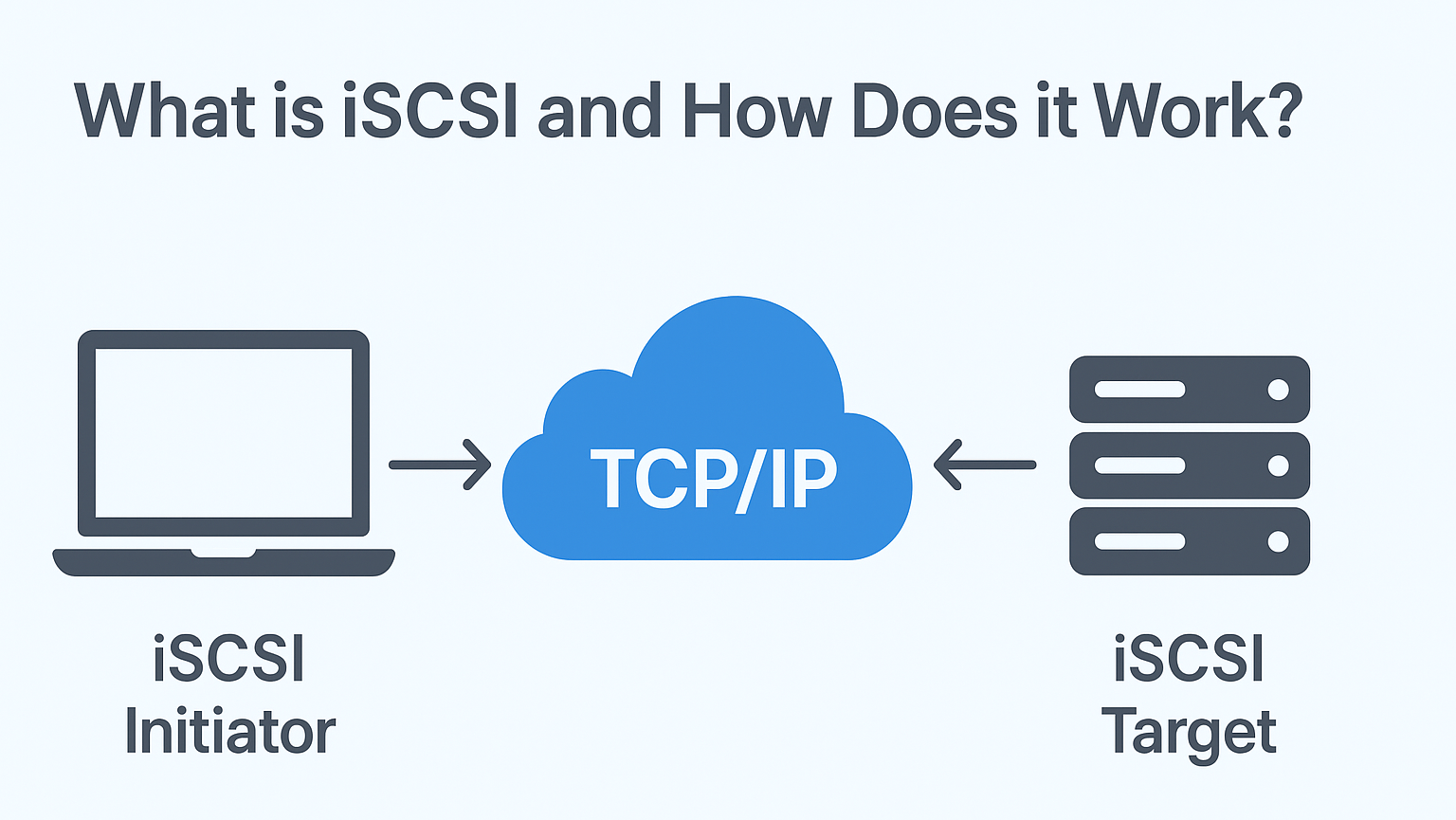
啟動器扮演用戶端的角色,向遠端儲存裝置請求儲存資源,讓您的系統可以像使用本機連接的儲存裝置一樣使用網路儲存裝置。.
目錄
iSCSI Initiator 如何運作
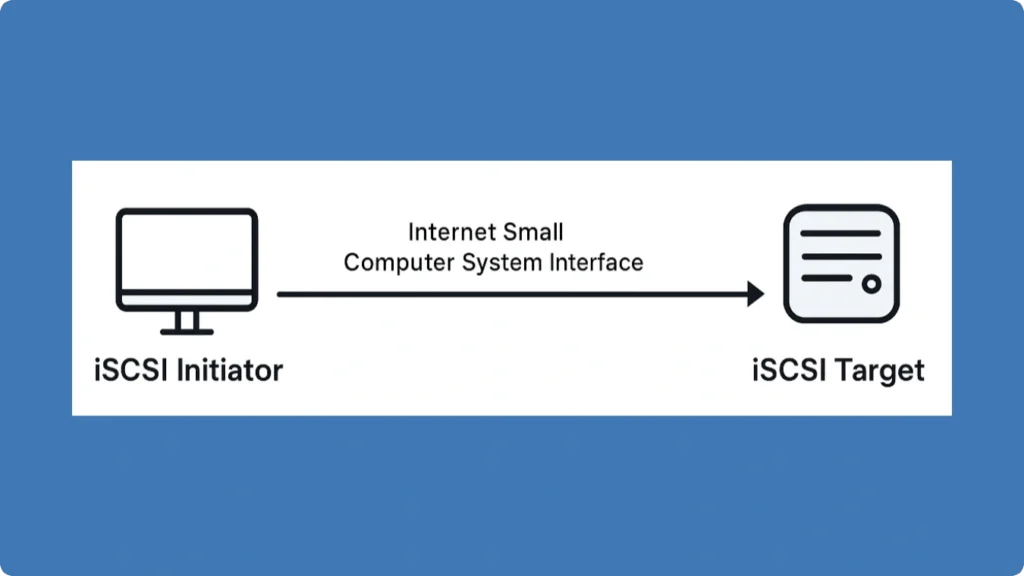
的 iSCSI 啟動器 與一個或多個 iSCSI 目標:
1. 安裝和設定啟動器:
在 Windows 上,透過控制台 > 管理工具存取內建的 iSCSI 啟動器。Linux 系統通常使用 Open-iSCSI。.
2. 發現目標:
在啟動器的發現索引標籤中輸入目標的 IP 位址或 DNS 名稱,以偵測可用的儲存裝置。.
3. 驗證連線(可選):
通訊協定支援 CHAP 驗證。如果需要,請輸入憑證。.
4. 連接和映射儲存:
經過驗證後,儲存啟動器會將目標的儲存對應為本機磁碟。. 格式化和分割儲存空間 根據需要。.
使用 iSCSI Initiator 的優點
● 經濟實惠: 使用現有的乙太網路基礎架構,無需昂貴的光纖通道硬體。.
● 集中管理: 整合 SAN 中的儲存空間,可從多個啟動器進行管理。.
● 彈性: 連接本機和遠端儲存設備;是虛擬化、備份和災難復原的理想選擇。.
● 擴充性: 輕鬆新增 iSCSI 目標,無需重新設定用戶端。.
iSCSI 啟動器使用範例
● 虛擬化: 透過儲存啟動器將多個虛擬機器連接到共用的 SAN 儲存。.
● 遠端備份: 使用此儲存通訊協定透過 WAN 存取儲存裝置,進行異地備份。.
● 企業儲存管理: 大型企業使用儲存啟動器,將伺服器有效率地連接至集中式儲存陣列。.
逐步教學:將 iSCSI 啟動器連接至目標 (Windows)
1.開啟 iSCSI 啟動器 從控制面板。.
2.前往 發現 索引標籤,然後按一下 發現入口網站, 然後輸入目標 IP。.
3.移動到 目標 索引標籤,選取發現的儲存裝置,然後按一下 連接.
4.啟用 持久連接 自動重新連線。.
5.在 磁碟管理 並將其格式化。.
iSCSI 硬碟機 vs 網路硬碟機
特點 | iSCSI 硬碟機 | 網路磁碟機 (SMB/NFS) |
存取層級 | 區塊層級 (行為類似本機磁碟) | 檔案層級 (需要檔案系統存取) |
效能 | 高效能,適用於資料庫和虛擬化 | 中度效能,取決於網路和檔案分享通訊協定 |
規範 | 網際網路小型電腦系統介面 | SMB (Windows) / NFS (Linux/Unix) |
使用個案 | SAN、虛擬機、備份、企業儲存 | 檔案共用、團隊協作、文件儲存 |
映射 | 在作業系統中顯示為本機磁碟 | 顯示為共用資料夾或網路路徑 |
彈性 | 可以分割、, 格式化, 並像本機磁碟一樣進行管理 | 僅限於資料夾層級作業,無法輕鬆託管可開機磁碟區 |
安全性 | 支援 CHAP 驗證、IPsec 加密 | 取決於檔案權限,可能需要 VPN 進行遠端存取 |
可以從網路磁碟機和 iSCSI 磁碟機復原資料嗎?
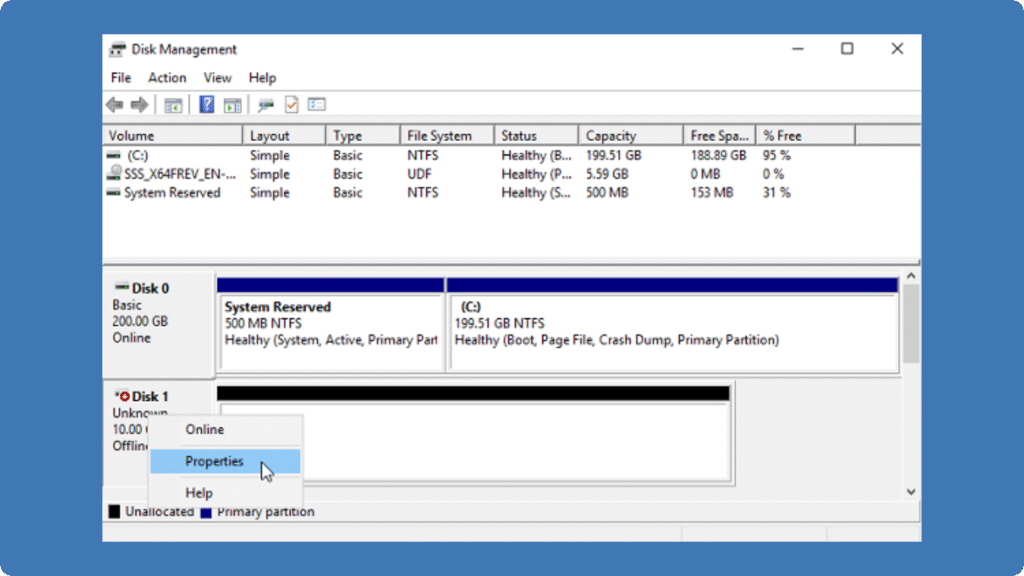
是的,通常可以從網路磁碟機和 SAN 磁碟機復原資料,但方法取決於儲存類型和故障情況。對於網路磁碟機 (例如 SMB 或 NFS 共用),刪除或遺失的檔案通常可以使用備份或檔案版本管理來還原。.
對於在作業系統中顯示為本機磁碟的 iSCSI 磁碟機或 SAN 儲存設備,由於下列原因而遺失的資料 意外刪除 或其他問題,只要將受影響的磁碟透過 SATA 或 USB 連接到健康的電腦即可復原。使用資料復原工具,例如 Amagicsoft’s Magic Data Recovery, 您可以掃描 iSCSI 磁碟機以尋找刪除的檔案、, 丟失的分區, 或損毀的資料,並有效地還原它們。.
iSCSI 啟動器常見問題
1.iSCSI 啟動器與儲存目標之間有何差異?
2.多個啟動器可以連接到同一個儲存裝置嗎?
3.網際網路小型電腦系統介面通訊協定是否安全?
4.使用儲存啟動器是否需要特殊硬體?
5.iSCSI 儲存協定可以透過網際網路運作嗎?
6.哪些作業系統支援儲存啟動器?
7.如何排除此儲存通訊協定的連線故障?
8.iSCSI 通訊協定的典型使用案例有哪些?
Erin Smith 是 Amagicsoft 公認最專業的作家之一。過去 10 年來,她不斷磨練自己的寫作技巧,幫助數百萬讀者解決技術問題。.



