What is iSCSI Initiator and How Does it Work?
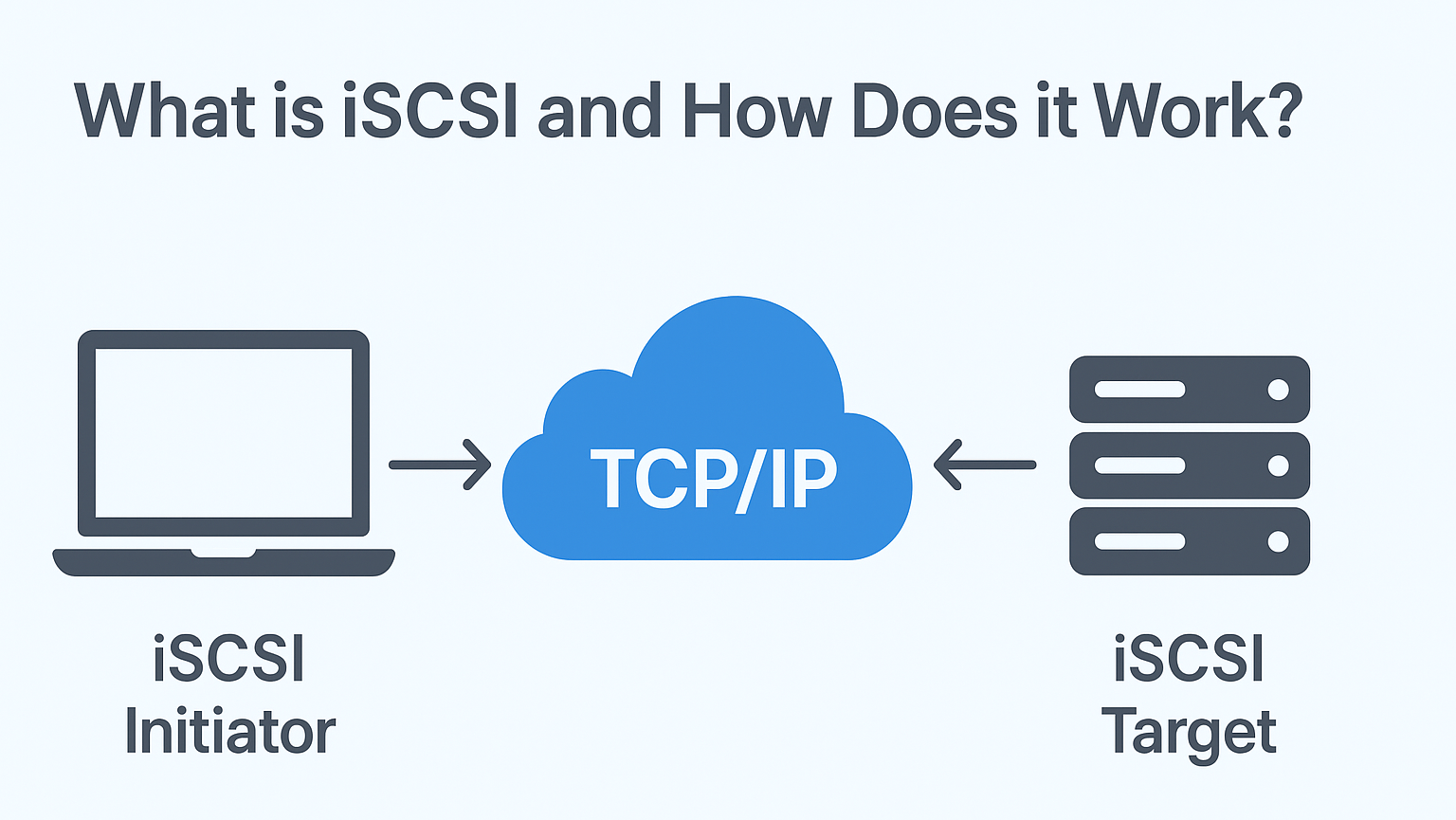
The Initiator acts as a client requesting storage resources from a remote storage device, allowing your system to use networked storage as if it were locally attached.
Table of Contents
How iSCSI Initiator Works
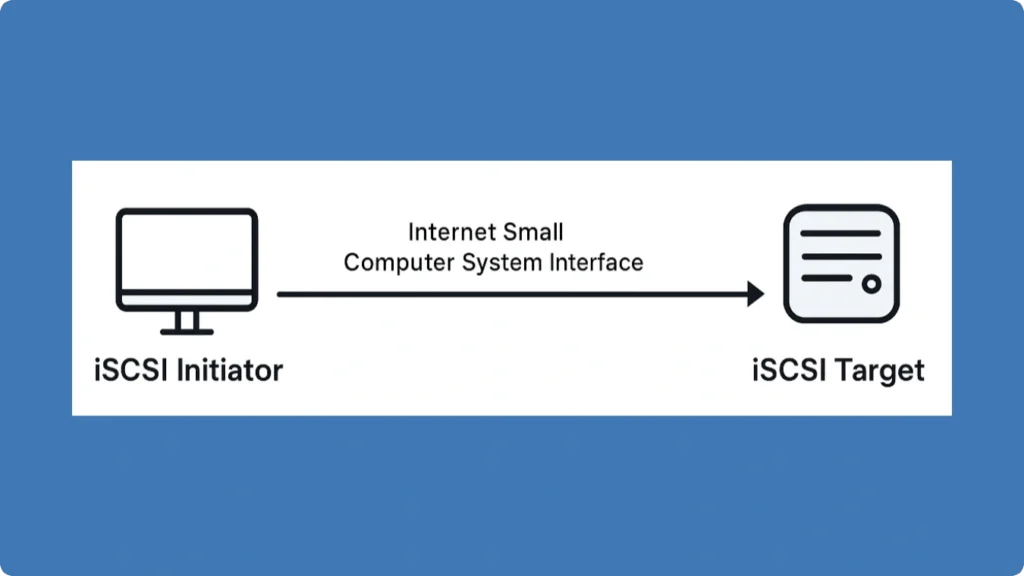
The iSCSI Initiator establishes sessions with one or multiple iSCSI Targets:
1. Install and Configure the Initiator:
On Windows, access the built-in iSCSI Initiator via Control Panel > Administrative Tools. Linux systems often use Open-iSCSI.
2. Discover Targets:
Enter the target’s IP address or DNS name in the initiator’s discovery tab to detect available storage devices.
3. Authenticate the Connection (Optional):
The protocol supports CHAP authentication. Enter credentials if required.
4. Connect and Map Storage:
Once authenticated, the storage initiator maps the target’s storage as a local disk. Format and partition the storage as needed.
Benefits of Using iSCSI Initiator
● Cost-Effective: Uses existing Ethernet infrastructure without expensive Fibre Channel hardware.
● Centralized Management: Consolidates storage in a SAN, manageable from multiple initiators.
● Flexibility: Connects both local and remote storage; ideal for virtualization, backup, and disaster recovery.
● Scalability: Easily add iSCSI Targets without reconfiguring clients.
Examples of iSCSI Initiator Use
● Virtualization: Connect multiple VMs to shared SAN storage via the storage initiator.
● Remote Backup: Access storage devices over WAN using this storage protocol for offsite backup.
● Enterprise Storage Management: Large organizations use the storage initiator to attach servers to centralized storage arrays efficiently.
Step-by-Step Tutorial: Connecting an iSCSI Initiator to a Target (Windows)
1. Open iSCSI Initiator from Control Panel.
2. Go to the Discovery tab and click Discover Portal, then enter the target IP.
3. Move to the Targets tab, select the discovered storage device, and click Connect.
4. Enable Persistent Connection for automatic reconnection.
5. Access the new disk in Disk Management and format it.
iSCSI Drive vs Network Drive
Feature | iSCSI Drive | Network Drive (SMB/NFS) |
Access Level | Block-level (behaves like local disk) | File-level (requires file system access) |
Performance | High performance, suitable for databases and virtualization | Moderate performance, dependent on network and file sharing protocol |
Protocol | Internet Small Computer System Interface | SMB (Windows) / NFS (Linux/Unix) |
Use Case | SAN, virtual machines, backup, enterprise storage | File sharing, team collaboration, document storage |
Mapping | Appears as a local disk to the OS | Appears as a shared folder or network path |
Flexibility | Can be partitioned, formatted, and managed like local disks | Limited to folder-level operations, cannot host bootable volumes easily |
Security | Supports CHAP authentication, IPsec encryption | Depends on file permissions, may require VPN for remote access |
Is it Possible to Recover Data from Network Drive and iSCSI Drive?
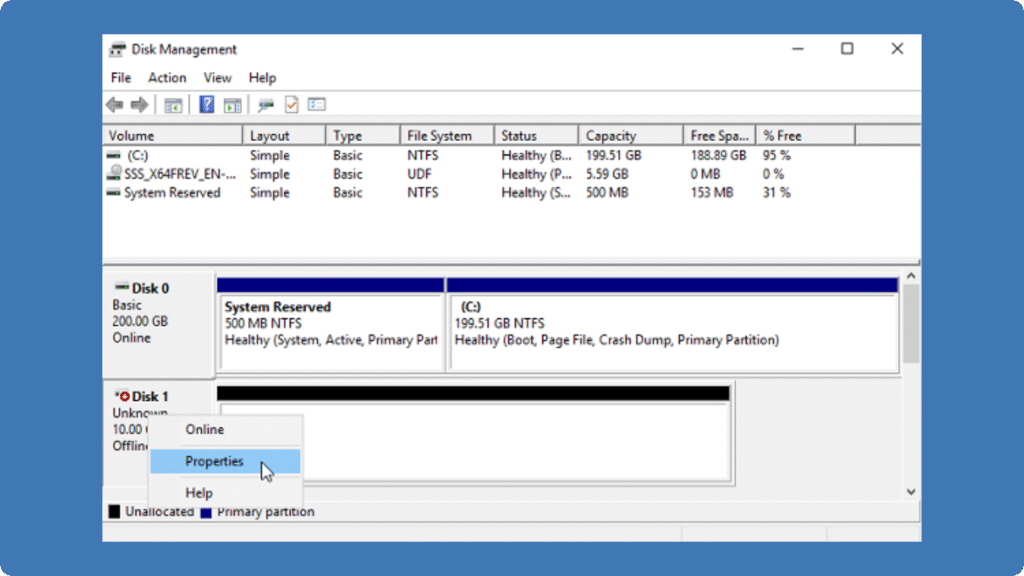
Yes, recovering data from Network Drives and SAN Drives is generally possible, but the approach depends on the storage type and failure scenario. For Network Drives (like SMB or NFS shares), deleted or lost files can often be restored using backups or file versioning.
For iSCSI Drives or SAN storage, which appear as local disks to the operating system, data lost due to accidental deletion or other issues can be recovered by taking the affected disk and connecting it to a healthy computer via SATA or USB. Using Data Recovery Tools, such as Amagicsoft’s Magic Data Recovery, you can scan the iSCSI drive for deleted files, lost partitions, or corrupted data and restore them effectively.
iSCSI Initiator FAQs
1. What is the difference between an iSCSI Initiator and a storage target?
2. Can multiple initiators connect to the same storage device?
3. Is the Internet Small Computer System Interface protocol secure?
4. Do I need special hardware to use a storage initiator?
5. Can iSCSI storage protocol work over the internet?
6. What operating systems support the storage initiator?
7. How do I troubleshoot connection failures with this storage protocol?
8. What are typical use cases for iSCSI protocol?
Erin Smith is recognized as one of the most professional writers at Amagicsoft. She has continually honed her writing skills over the past 10 years and helped millions of readers solve their tech problems.



