Decryption

Table of Contents
What Is Decryption?
At its core, Decryption is the act of reversing encryption. A protected volume or file can only be opened when the correct key—such as a password, recovery key, digital certificate, or software license—is supplied.
Because many systems rely on encryption for security, understanding this process helps avoid data loss during recovery or migration.
Common situations where users may need to unlock encrypted data include:
① Accessing BitLocker-protected drives
② Opening password-secured archives
③ Restoring software activation keys after a reset
④ Reading configuration files that were previously encrypted
How the Decryption Process Works Internally
Although encryption technologies differ, most follow a similar logic:
① Encrypted data is provided
② A matching key is entered
③ The algorithm checks whether the key is valid
④ The system outputs readable information when the key matches
Technologies such as AES and RSA rely on strong cryptographic structures. The user, however, only needs the correct key to restore access.
Why This Process Matters
Unlocking protected data is a critical part of system maintenance and recovery. Proper handling enables:
① Smooth system reinstallation or migration
② Recovery of activation information for licensed software
③ Access to essential files stored on encrypted disks
④ Restoration of configurations and credentials after errors
Because more devices use encryption by default, understanding proper unlocking methods is increasingly important.
When Access Fails Due to Lost Decryption Keys
A common cause of decryption failure is a missing key. This may occur after:
① A system crash that resets stored credentials
② Windows reinstallation
③ Drive migration to another computer
④ Forgetting where a recovery key was stored
Users often believe the data is gone permanently, but that is not always the case.
Safe Ways to Recover Lost Keys (BitLocker, Windows, Office, etc.)
If the required key cannot be found, a safe recovery method becomes necessary.
A practical solution is Magic Recovery Key, which helps retrieve BitLocker recovery keys, Windows product keys, Office activation keys, and other license information stored in system files.
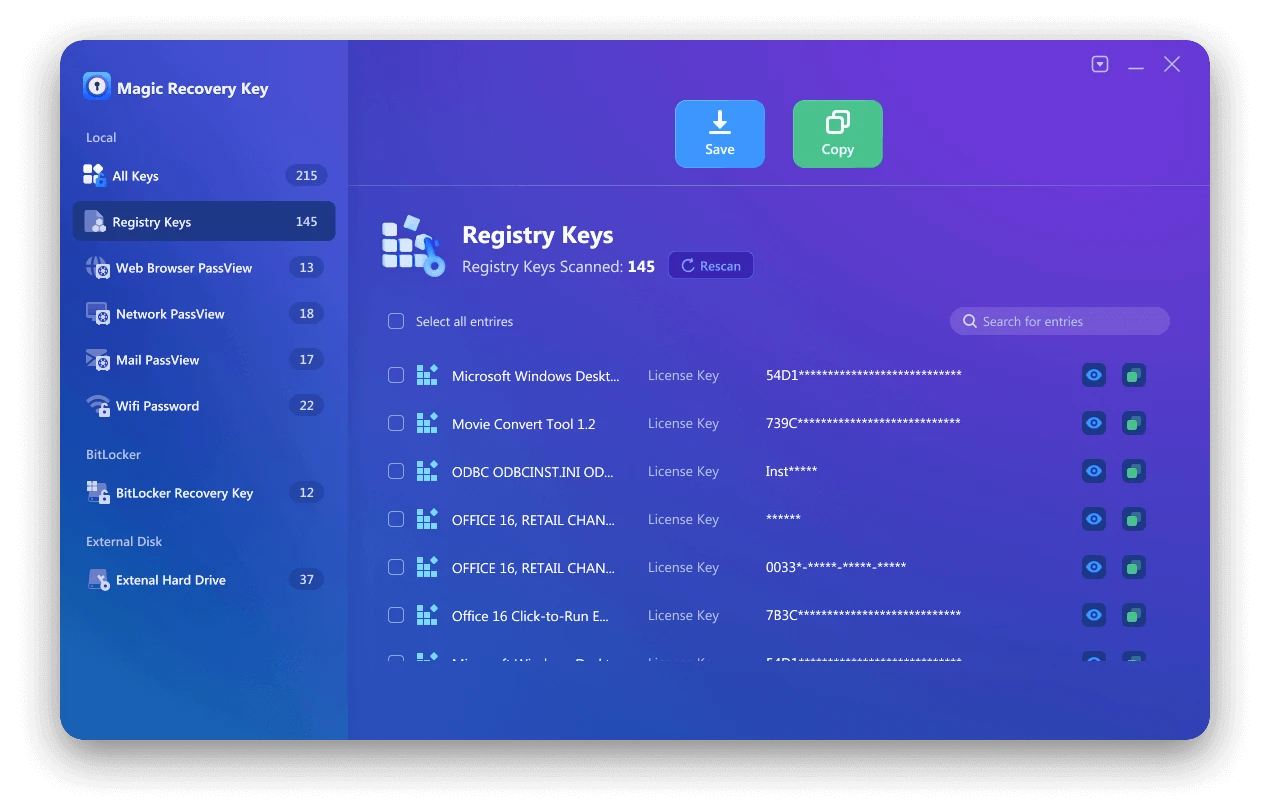
How to Recover Keys Using Magic Recovery Key
① Install and open Magic Recovery Key
Supports Windows 7/8/10/11 and Windows Server
② Choose the type of key to recover (BitLocker, Windows, Office, etc.)
③ Run a full system scan
④ View the keys found in the results
⑤ Export them for safekeeping
Because the software operates in read-only mode, it avoids modifying encrypted data.
Limitations You Should Know Before Attempting
Even with proper tools and knowledge, some limitations apply:
① A valid key is always required
② Damaged drives may block access
③ Certain systems restrict repeated attempts
④ Encrypted files cannot be opened if metadata is corrupted
Being aware of these constraints helps users choose appropriate solutions.
Conclusion
Although encryption protects privacy, the ability to unlock data when needed is equally important. When keys are missing, a safe tool such as Magic Recovery Key can assist by locating BitLocker and software license keys required to regain access without risking data integrity.
If you cannot open encrypted data because the original key is unavailable, you may consider using Magic Recovery Key. It offers a safe and non-intrusive way to retrieve the information needed to unlock protected drives and licensed software.
Supports Windows 7/8/10/11 and Windows Server
Decryption FAQs
What does this process do in computer systems?
Why do some encrypted drives require a recovery key?
Can encrypted content be accessed without the right key?
How can I find a missing BitLocker recovery key?
Does unlocking protected data damage the files?
Why does unlocking sometimes fail repeatedly?
Are software license keys important during system recovery?
Is Magic Recovery Key safe to use?
Erin Smith is recognized as one of the most professional writers at Amagicsoft. She has continually honed her writing skills over the past 10 years and helped millions of readers solve their tech problems.